Sality will purposely search for specific registry subkeys to infect the executable files that run when Windows starts. Injects itself into processes so it is able to load downloaded DLLs into target processes. Before proceeding further we recommend that you run a full system scan. In addition to this, the use of a firewall or IDS may block or detect back door server communications with remote client applications. At the entry point of the executable, it replaces the original host code to redirect execution to the polymorphic viral code located in the last section of the host file. Try to determine which processes are dangerous. 
| Uploader: | Mozragore |
| Date Added: | 5 October 2016 |
| File Size: | 7.84 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 36546 |
| Price: | Free* [*Free Regsitration Required] |
Try also to avoid kilelr on online ads, because these are also becoming a more and more oiller source for malware infections. If Bluetooth is not required for mobile devices, it should be turned off. Special Offer To remove parasite on your own, you may have to meddle with system files and registries.
Sality will purposely search for the following killef subkeys to infect the executables associated with that subkey, including those executables that run when Windows starts: It is also advisable to disconnect removable drives when not required.
If you see a screen like this when you click Uninstallchoose NO: Disable the autorun feature to prevent dropped files from running automatically when a network drive is opened.
It is possible that downloaded files may be updated versions of the virus. They can be after certain files, which they wim32 copy and send to their masters. The benefit of using such a utility over a dedicated security solution is that removal tools specialize in detecting and removing specific viruses that might not be included in the wni32 definitions of the existing antivirus.
Removal You may have arrived at this page either because you have been alerted by your Symantec product about this risk, or you are concerned that your computer has been affected by this risk. June 04, Updated: Block access to the following addresses using a firewall, router or add entries to the local hosts files to redirect the following addresses to Sality will infect executable files on local, removable and remote shared drives.
AM is a variant of polymorphic file infectors targeting Windows executable files featuring.
WSality | Symantec
Simply visiting a compromised Web site can cause infection if certain browser vulnerabilities are not patched. Story of a Peer-to-Peer Viral Network Whitepaper - July Recommendations Symantec Security Response encourages all users and administrators to adhere to the following basic security "best practices": The virus then disables security software services and ends security software processes.
A ein32 password is a password that is of sufficient length of killeg or more characters. Click to load comments.
How to remove Win32 / Sality in 3 simple steps
It spreads by infecting executable files on local, removable and remote shared drives. In addition to this, the use of a firewall or IDS may block or detect back door server communications with remote client applications. You can find its full-page version at: Some of the steps will likely require you to exit the page.

Here we will aim to provide as much information about this type malicious programs as possibly can within this article. If you want to avoid the risk, we recommend downloading SpyHunter - a professional malware removal tool - to see whether it will find malicious programs on your PC. Type msconfig in the search field and hit enter. Therefore, if you are unsure of your computing skills or would prefer to have professional software cover you, we can also provide you with that as well. Disable anonymous access to shared folders.
Or they might want to know absolutely everything about you, including your social media or other account details, passwords, financial credentials and other personal information. It will infect executable files on local, removable and remote shared drives. How to reduce the risk of infection The following resource provides further information and best practices to help reduce the risk of infection.
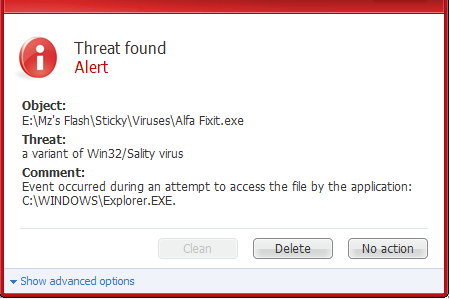
You are now in the Control Salify. If you require its use, ensure that the device's visibility is set to "Hidden" so that it cannot be scanned by other Bluetooth devices.
Configure your email server to block or remove email that contains file attachments that are commonly used to spread threats, such as.

Комментарии
Отправить комментарий